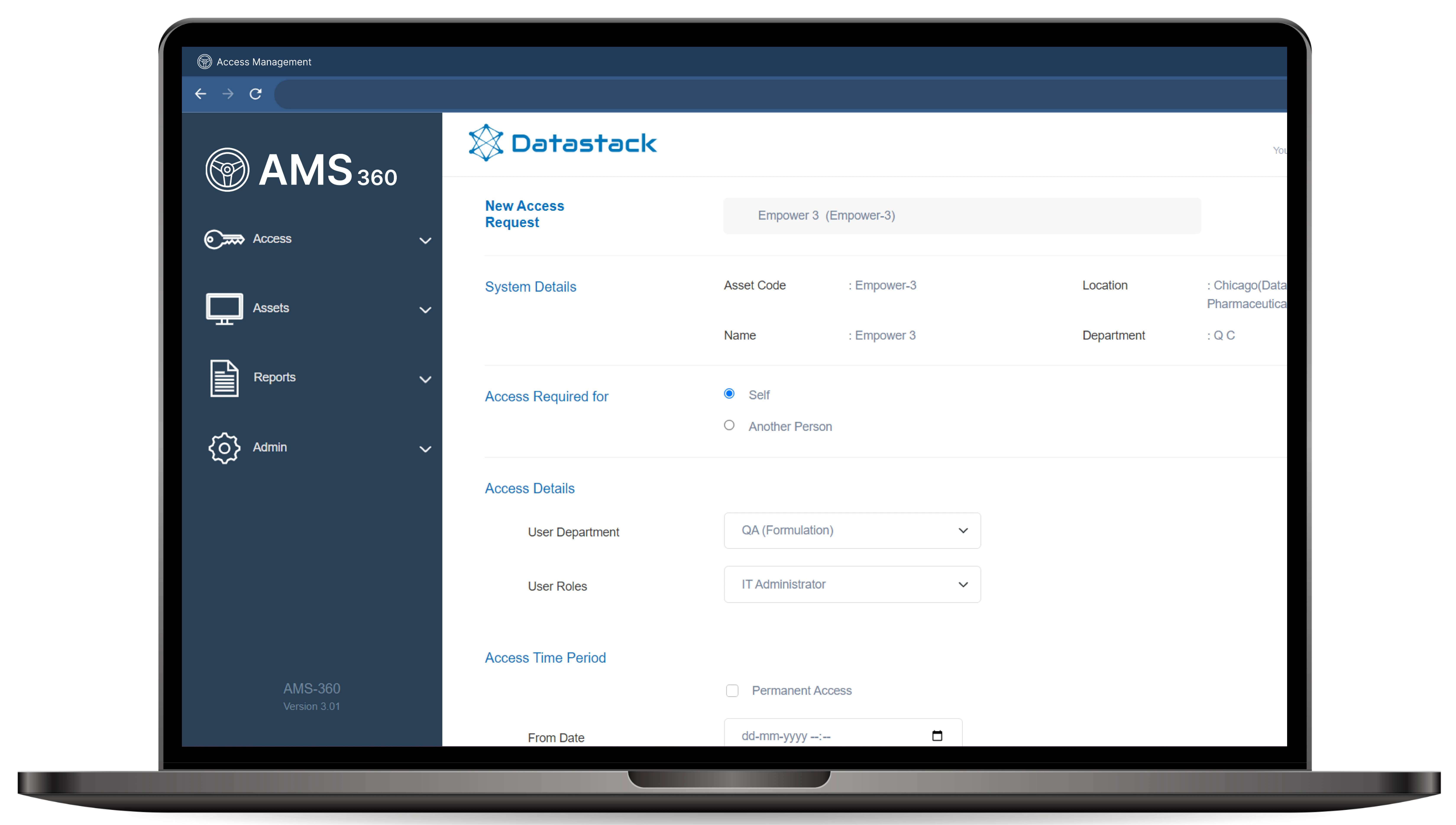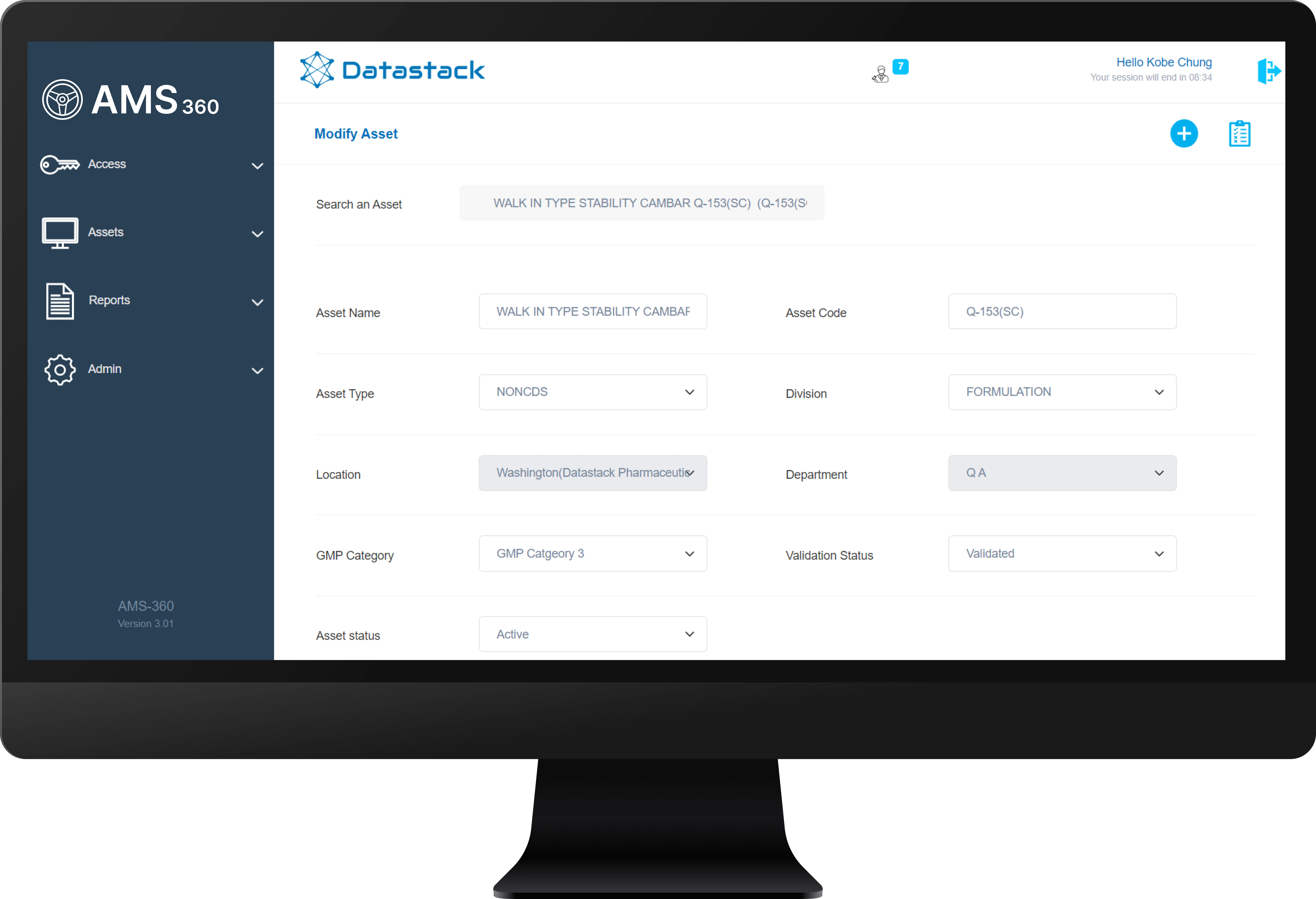

Access Management Redefined
AMS 360 enables you to simplify, streamline and track access to all your computer systems in accordance with GxP guidelines.


AMS 360 enables you to simplify, streamline and track access to all your computer systems in accordance with GxP guidelines.

Digitize your access control and access monitoring in accordance with CGMP guidelines

Know accurately who has access to what system and optimize software licenses

Never worry about lingering access and associated risks of loss of Intellectual Property or loss of Data Integrity
Keeping track of who has access to what system, using manual process, is cumbersome. Inability to control and monitor real-time access increases vulnerability of integrity and security issues, leading to non compliance to regulatory guidelines
AMS 360 enables you to simplify, streamline and track access to all your computer systems. It helps your firm demonstrate compliance to the GxP regulations